Who Is responsible For Security in the Cloud?
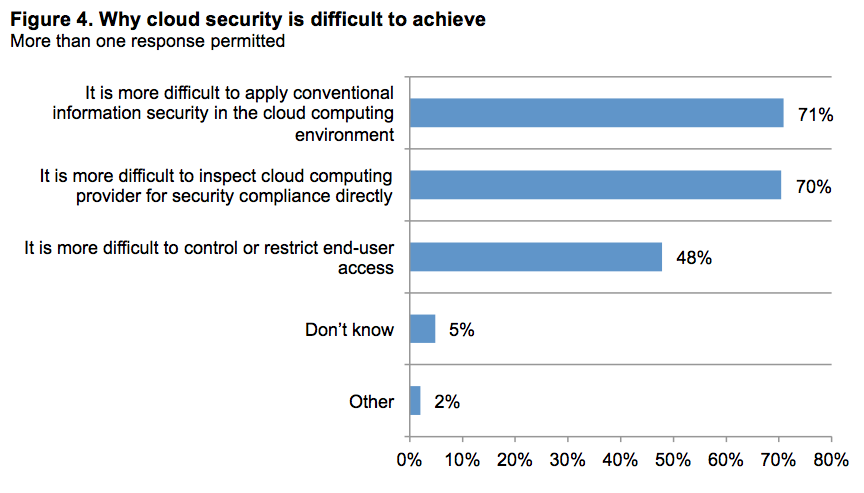
What do IT professionals believe to be the hardest part of dealing with security in the cloud. Source: Ponemon Institute
The cloud has achieved mainstream status and most companies have at least some cloud footprint by this point. As with all things technology the question of security only seems to come up after the fact. So, now that companies are working with cloud service providers there is a potential conflict over who should be accountable for making sure the cloud is secure.
Armor—formerly FireHost—sponsored a Ponemon Institute study called Cloud Security: Getting It Right to explore this issue and learn more about the state of cloud security. The report is the result of surveying 990 IT professional managers and executive leaders from organizations that process business-critical data in the cloud or store sensitive business data in a cloud environment.
When an organization purchases cloud services or infrastructure from a third-party provider who is responsible for security? Should the cloud service provider ensure the environment and applications are secure, or is the business itself still responsible for its own security even in the cloud? Or is it somewhere in the middle—and if so, how do you draw the line to distinguish between which entity is responsible for which elements of security?
Cloud Security: Getting It Right uncovered some concerns when it comes to this quandary. More than 60 percent of respondents indicated that security is rarely or never a consideration when evaluating cloud services. Only 15 percent believe that the onus for securing SaaS (software-as-a-service) applications falls on the company’s own IT security team.
Some of the key findings from the study are:
- Fifty-six percent of respondents say the ability to save money is by far the primary reason to use cloud resources
- Only 33 percent of respondents say they have confidence they are meeting security objectives in the cloud
- Seventy-nine percent of respondents say security is important always or most of the time; 74 percent say compliance is considered important always or most of the time
“It is alarming to me that 56 percent of respondents say they are unwilling to pay a premium to ensure the security of sensitive data in the cloud,” declared Jeff Schilling, CSO of Armor. “I believe there is a missed opportunity to get the initiative back from the cyber threat who has owned the good guys for more than 10 years. Virtualization and cloud architecture gives the good guys the opportunity to censor and build a secure environment that puts the threat at a disadvantage. However, the data shows most don’t want to invest in a secure solution and are doomed to repeat the mistakes we made in the network-centric build-out of the Internet.”
CSO Online: http://bit.ly/1MQ6uel


























