"Torus" Reveals an Expansion in 5 Eyes Surveillance.
In a guest opinion post for WIRED, journalist and researcher Duncan Campbell describes how a one-word clue in a document leaked by NSA whistleblower Edward Snowden may have revealed a massive increase in the surveillance capacity of GCHQ and other spying agencies.
Campbell is a named contributor in the report, published on 28 May 2015 by the Nautilus Institute of Berkeley, along with Desmond Ball, Bill Robinson and Richard Tanter.
The world of massive communications surveillance that former intelligence contractor Edward Snowden has exposed since 2013 in fact began more than 50 years ago, as soon as western nations first connected across the oceans using geostationary satellites.
At that time the US paid for allies, mainly Britain, to build the ECHELON spy network of tracking dishes, according to published memoirs and published documents leaked by Snowden. Britain's electronic listening agency GCHQ copied what the satellites sent, and sent what the US wanted back to America, including -- until 1974 -- unlawful material about its own citizens.
On Sunday May 31, the US Senate is to hold a last minute emergency debate about whether to kill the Patriot Act's powers to collect all Americans' telephone records -- but it has taken 50 years to catch up. Legal restrictions purportedly put in place on NSA after the Watergate scandal of the 1970s have proved ineffectual.
When optical fibre submarine cables replaced satellites to form the intercontinental backbone for the Internet, the snoopers moved over and tapped fibers instead. Few now remember "Early Bird" (Intelsat 1) in the 1960s, or the ever-bigger communications satellites (COMSATs) that followed. Or so it seemed, until an international group of spy agency watchers, including myself, compared notes and realised that another great eavesdropping expansion has been taking place in plain sight.
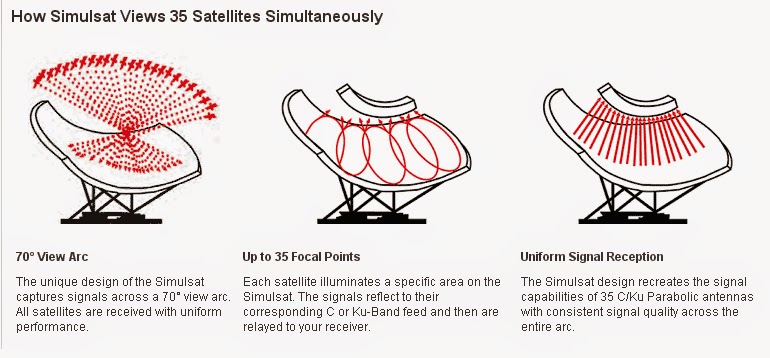
We were alerted by just one word, published in a Snowden slide a year ago, explaining a new plan by the so-called "Five Eyes" listening agencies to "Collect It All". The word was "Torus". In literal terms the word can mean "doughnut", though from the slide it appeared that this doughnut has special properties -- namely being a critical new means by which to grab all of the world's communications that still travel through space. "Torus increases access", one cryptic slide suggested. Torus is a brand new kind of satellite espionage, capable of soaking up calls and messages and data from 35 satellites at once. The dishes themselves don't look too different to familiar space tracking dishes, and can be hidden inside giant white globes -- radomes. But look more closely and the power of the doughnut emerges.
Specifically, a Torus dish can monitor 70 degrees of the sky, without moving. Mathematically, the dishes are a combination of a parabola with a sphere, shaped to relay multiple signals focused from space into an array of different listening horns. Once collected all the different facets of modern communications, from Facebook to fax, are separated and sifted and filed away in giant data centres, such as NSA has recently built near Salt Lake City.
Over the last eight years, we believe our research shows, western spy agencies have built six new Torus collectors in the UK, Cyprus, Oman, Australia and New Zealand. Their locations are diverse: deep in the Australian outback, in Lord of the Rings territory in New Zealand's South Island, and on the Devon coast in England.
About 400 commercial communications satellites now orbit over the equator 24,000 miles above the Earth's surface, carrying data and telephone signals to remote areas, ocean cruise liners, and privileged passengers in the air. All are targets for what a leaked NSA document calls the "New Collection Posture".
The agencies already have more than 200 traditional tracking dishes scattered around the planet -- we counted them all, using Google Earth and other online image sites. The online images show that numbers of listening dishes have doubled since about 2000. The six new doughnut dishes can double this up again, and "collect-it-all", as claimed in Top Secret Snowden slides, potentially increasing snooping capacity by up to 200 satellites.
But the Russians got there first, we found. The grandmother of all doughnut dishes had been built first by the former Soviet intelligence service in the final years of the Cold War, before 1990. Lurking in Ukraine wheat fields 15 kilometers from the Black Sea port of Odessa, the Ovidiopol-2 spy base may once have been the electronic jewel in the KGB's crown. Former Russian spies say they called it "the Comb".
Standing 10 storeys high and 80 metres across, the Ovidiopol-2 listening antenna appears to have been equipped to track at least 20 western satellites at once. After the USSR broke up, it was handed over to the Ukraine government's foreign intelligence service (SZRU). The site is still in use, and now includes a second Torus.
Meanwhile Britain's own satellite intelligence gathering is less secret than ever; the original "Five Eyes" satellite monitoring project -- ECHELON -- has become widely known after European Parliament enquiries into satellite monitoring from 1999 to 2001.
After the controversies subsided, however, the stations kept getting larger. In 2004, the German foreign intelligence agency BND took over NSA's large FORNSAT site at Bad Aibling, Bavaria), but continued to allow NSA remotely to task "selectors" to the equipment operated at the site. In April this year, a German parliamentary enquiry determined that BND had improperly allowed NSA to use tens of thousands of selectors to collect intelligence on the European Commission, and other European government and commercial targets. Other reports quote claims by BND staff that some improper and potentially unlawful targeting by NSA had been detected and blocked.
Mass surveillance of satellite communications has grown. There are now 232 antennas available at the sites identified, almost double the capacity before 2001. The unique new aerials mean that the potential capacity has quadrupled.


























