The Robots Taking Your Job Could Get You Killed
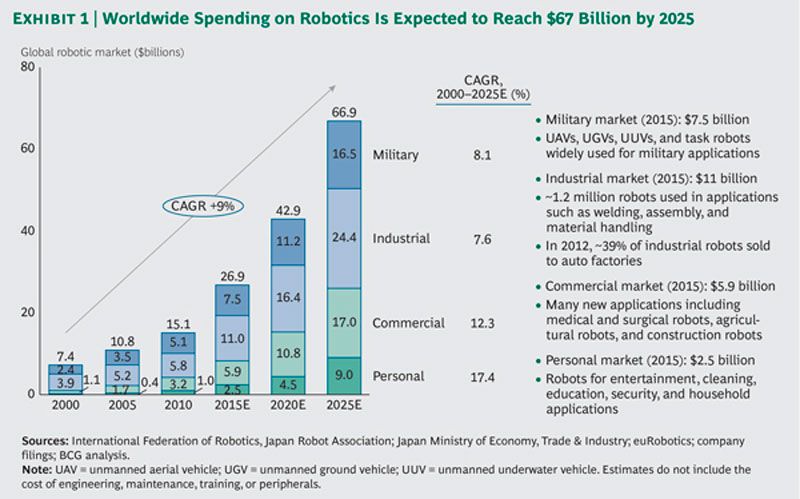 Boston Consulting Group recently released a global robotics market study that projects industry growth of 10.4% CAGR.
Boston Consulting Group recently released a global robotics market study that projects industry growth of 10.4% CAGR.
The rush to automate more factory processes may look like it’s saving money, but to Ken Westin, a senior security analyst at Tripwire, it’s a dangerous trend that’s spreading cyber vulnerabilities across entire industries. And it will only get worse. Westin says that too much or unsafely implemented automation in chemical and pharmaceutical plants will result in a catastrophic, and largely avoidable, cyber attack in the next two years.
That automation is on the rise is no secret. Boston Consulting Group has forecast that between this year and 2025,1.2 million industrial robots will make their way into factories across the United States (in addition to those in factories today.) Some projections commonly cited among the chemical and pharmaceutical industry suggest that automation in more factories could increase throughput by 20 percent on a yearly basis and reduce energy consumption by 8 percent.
“A lot of businesses see value in automating a lot more of the processes when it comes to manufacturing,” Westin said at the Black Hat cybersecurity conference here. “They’ll actually let a lot of these people go, like the engineers. And they’ll focus on the automation. What they fail to do is look at the increased risk that that poses to the organization.”
“These systems were designed decades ago,” he went on. “They’re using protocols that are pretty ancient. They were designed for reliability and efficiency. Security was not a part of that. The security occurred on the physical end, protecting people who came in and out of these physical systems. Once you connect that to a corporate network? What happens is the corporate network now gets connected to the manufacturing plant, which was not designed to be connected to the Internet at all. When you have that connection that increases risk to the organization. That’s something that’s not assessed in their analysis of risk.”
How ubiquitous is open Internet connectivity in supervisory command and control systems? You would be surprised. “Where and when something happens is almost completely under cyber control,” said Jason Larsen, a principal security consultant at the group IOACTIVE. “Opening and closing valves is almost always under cyber control.” Larsen spoke during a demonstration that showed how un opening and closing of valves can cause heat and pressure buildups as well as massive container destruction, and leaks of volatile or poisonous chemicals.
Of course, you, as the plant operator, could just call in engineers to monitor or fix the problem, but you fired them to save money, remember? Westin calls it “a perfect storm in a lot of ways.” He predicts the compromise of a major manufacturing plant in the next two years. “It will be something where we see a loss of life. That’s going to change everything.”
While his clients trend toward energy companies, it’s the chemicals and pharmaceutical plants that cause him the most stress. He singled out companies like Bayer and Pfizer, based just outside of Pittsburgh, as particularly attractive targets. “I flew into Pittsburgh and looked down at some of these plants along the river. Imagine the environmental impact if some of chemical leaked out?”
It’s that classic cyber-Pearl-Harbor scenario that former Defense Secretary Leon Panetta warned of in a 2012 speech, and which has since prompted massive increase in cybersecurity spending, much to the benefit of people like Westin. But he says many companies could implement solutions to fix some of these vulnerabilities themselves, do so quickly, and at not necessarily by hiring a fancy hacker team to hunt for bugs. For starters, simple two-factor authentication and other means to keep passwords safe should be much more common. They’re exactly the sorts of measures that the Office of Personnel Management was able to quickly put in place after a major breach. Westin says that password and credential loss is the most common major vulnerability and a lot of that springs from human error, rather than brute force attacks, that don’t use stolen credentials.
Humans are the solution, but they’re also still the problem.
DefenseOne: http://bit.ly/1WoONX4
























