IBM Breakthrough In Quantum Computing
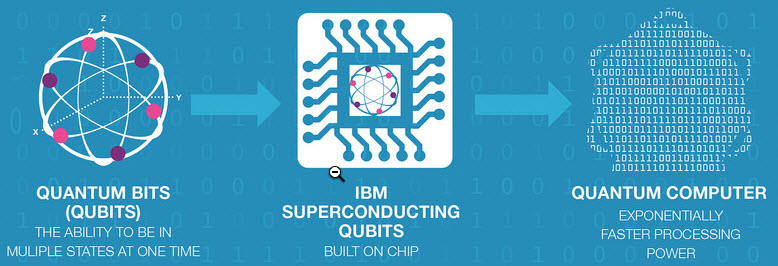
IBM scientists have announced the two primary advances towards the quantum computer’s practical realizations and currently, they have found out how to detect and measure the quantum errors in a simultaneous manner. The main problem in the breed of future computers is that, they are using qubits rather than using normal bits, qubits are commonly referred as quantum bits and these bits are normally represented in a 0, a 1 and sometimes both. When two of them get existed at the same time, they are referred as phase relationship.
In quantum computers, the main problem arises when two qubits already exist in the same state, it is far impossible to detect the errors between them simultaneously. It is highly necessary to find out all the errors that are present to improve work reliability. The researchers at IBM have cracked a solution for this, with the use of Moore’s law.
The breakthrough is described in the journal Nature Communications, issued on April 2015 and they explained how to detect and measure two types of quantum errors, that generally happens in real quantum computers.
Arvind Krishna, senior vice president and director of IBM Research said “Quantum computing could be potentially transformative, enabling us to solve problems that are impossible or impractical to solve today. While quantum computers have traditionally been explored for cryptography, one area we find very compelling is the potential for practical quantum systems to solve problems in physics and quantum chemistry that are unsolvable today. This could have enormous potential in materials or drug design, opening up a new realm of applications.”
Till now, it is only possible to detect only one type of error, and an IBM researcher has finally made a solution, that offers an immense step towards real quantum computers. The findings will be a better for building real quantum computers in the future. Hope this will definitely help quantum computers to gain more audience, in the world that is consumed by Big Data, and help us to store some larger databases as well as unstructured data over it.


























