How to Stalk Someone’s Location on Facebook
Once again, warnings are being given that Internet users may not realise just how much personal information they are sharing with others online – and this time it’s about where you spend your life working, playing and sleeping.
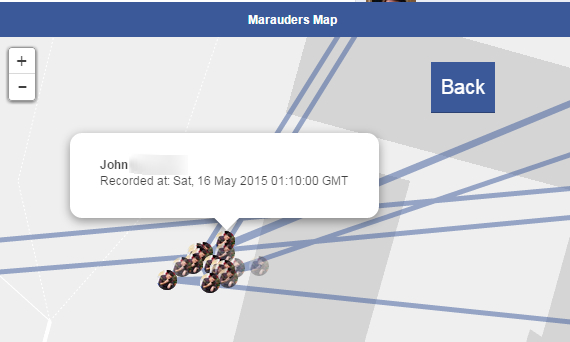
A newly released tool lets you easily track the movements of other Facebook users and plot them on a map, by scooping up the location data they have shared in Facebook Messenger chats.
Marauder’s Map is named after a magical chart from the Harry Potter novels that shows the location of every person in the grounds of Hogwarts School.
But the new Marauder’s Map is real, not fictional.
Initially released by Harvard College computer science student Aran Khanna as a Chrome browser extension, Marauder’s Map makes it child’s play for anybody to become a stalker – finding out a contact’s place of work, where they live, or favourite bars and hangouts.
Marauder’s Map scrapes the location data from your Facebook Messenger page, and plots it on a map. In a blog post, Khanna describes Marauder’s Map as having “creepy potential”:
“The first thing I noticed when I started to write my code was that the latitude and longitude coordinates of the message locations have more than 5 decimal places of precision, making it possible to pinpoint the sender’s location to less than a meter.”
In one example, Khanna describes how he was able to use Marauder’s Map to determine where a casual acquaintance slept at night:
“I am in a pretty active group chat with some of my brother’s friends (who I am friends with on Facebook but don’t know too well). They are all fairly active on the chat, posting once a day or more.”
“Let’s pick on the one who goes to Stanford. By simply looking at the cluster of messages sent late at night you can tell exactly where his dorm is, and in fact approximately where his room is located in that dorm.”
Deeper analysis of data collected in this way begins to draw up a clear picture of people’s schedule: where they work, where they drink coffee, where they go the gym, where they sleep…
You may not have even realised that your friends’ location information was being shared in the conversations you had via Facebook Messenger, as there is no visual sign.
It’s only when you click on their speech bubble that you discover that embedded into the chat is location data, which reveals where the sender was with creepy accuracy. One issue is that you may think it’s harmless to attach your location to a single message, but – unless you remember to disable location sharing afterwards – it’s all too easy for an archive of your past locations to build up.
And, as far as I can tell, there is no way to delete the location data from past messages you have sent.
Such creepy collection and examination of location data has clear implications for not just consumers, but also businesses.
If your company is being targeted by criminals they may attempt to learn the schedules of your workers – hoping to launch man-in-the-middle attacks over unsecured WiFi in coffee shops, or determine the home addresses of senior executives. All they would need to do to begin to collect the data is start an online chat with you, perhaps posing as a potential customer or romantic interest.
The potential for abuse, whether it be by organised criminal gangs targeting an enterprise, or jealous former partners and obsessive stalkers, should be clear. Which means that consumers and businesses alike should consider disabling Facebook
Messenger’s ability to track and share your location.
Don’t wait. Check that the phones you own, or the ones you’re responsible for protecting in your business, aren’t sharing any information, which they don’t need to – which includes, of course, their location.


























