Hacking For Cause: Growing Cyber Security Trend
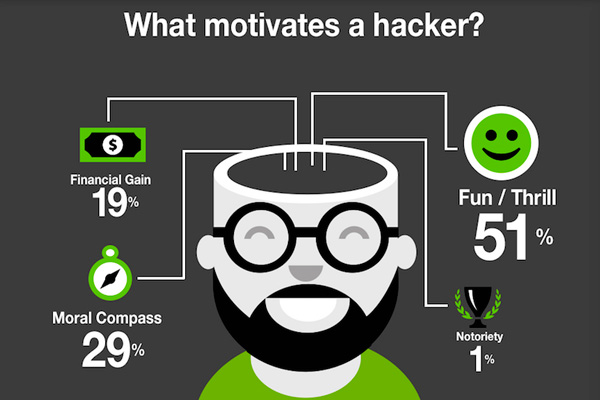
Why do people hack?
What do the following data-breach headlines from the past year have in common? The Sony Pictures hack: Everything we know so far; Anonymous hackers release emails ordering bear cubs be killed; Hackers threaten to release names from adultery website; How Latest Snowden Leak Is Headache for White House; How DID hackers steal celebrities’ private iCloud photos? Connecting the dots yet? If not, here are a two more headlines to tip you off: Hackers Remotely Kill a Jeep on the Highway – With Me in It and Hacktivists taking aim at Dallas-Fort Worth police departments.
No doubt, there are several similarities to these data-breach headlines. The sophistication of these cyber attackers and the lack of an adequate cyber defense are common themes in these stories.
But there is one overriding theme. I call this new trend: “Hacking for a cause.”
The reason? The hacker motive for these data breaches is not (primarily) financial gain. No doubt, someone, somewhere, may have made money in the process — especially if a hired hacker was doing the hacking actions for someone else.
Why is the motive of the hacker a significant issue?The past decade of data breaches has been dominated by the conventional wisdom and this public perception: “Follow the money.” Specifically, organized bad-guy hacker criminals are looking to rob banks, steal intellectual property, get your social security number, steal credit card numbers or gain your logon credentials to ultimately get to your cash — or better yet, your organization’s cash.
Of course, there also is a second, less talked about hacking theme around protecting critical infrastructure from bad guys to ensure that utilities, like our lights, stay on and planes don’t fall out of the sky. The Jeep hackers might even fit into this second category, but let’s move on.
Without a doubt, the mainstream perception about these “bad guys” illegally breaking into big databases full of sensitive personal information is still the primary hacking challenge for law enforcement agencies around the world.
But our new reality is becoming much more complex.
Sure, there are plenty of organized criminals still seeking to rob banks and get sensitive company secrets for competitive gain. But this new “hacking for a cause” trend, with motives beyond stealing to enrich oneself, will be a significant “game-changer” for society. The implications are as vast as the number of social causes and beliefs that exist.
For example, some common causes that Philanthropedia lists include: violence against women, climate change, criminal justice and access to healthy foods — to name just a few.
A new world of hacking motives is starting to emerge — along with convenient, easy to use tools for computer novices to do many dangerous things online.
You can add access to the political agendas of the left, right and center. Infiltration of an individual’s religious leanings. Intrusion of a family run company’s opinions regarding abortion or gay rights. Subversion to the trillions of files, pictures and recordings used for a limitless number of topics, such as divorce proceedings.
You begin to see where I’m going. Bottom line, everyone has causes they champion, information they want and certain data that is just beyond their grasp. The new thinking is becoming: What content do I wish I had? How will I get it? Who can acquire it for me?
Why Should We Care?
Why should we fear this trend? There is an evolving definition of right and wrong regarding hacking.
For example, I may think that Edward Snowden stealing NSA records was wrong. However, I may also agree that the information he disclosed was valuable to society to help protect online privacy. Although I do not believe that the ends justify the means, millions of Americans now believe that Snowden was a hero. In their view, the ends do justify the means in his case. Bottom line, they think his illegal actions were justified.
Another hacking example comes from the recent Ashley Madison story. Many Americans think that Ashley Madison customers got what they deserved. The business they are in is so bad that “those scoundrels deserved to be hacked along with the resulting consequences.”
I’ve heard dozens of people say if your name was in that “horrible database” … you deserve to “have your information released on websites and face the shame. Let them go explain it to their spouses.”
But take a step back and see where this is taking us. We are heading toward a world where it is ok to hack, as long as your cause will be helped. Or, in other words, “If my cause is more important than the law or company policy — hacking for the data I want is fine.”
No doubt some people will like or dislike various causes. Important ideas to champion come from the left, right and center of the political spectrum. No one is exempt. “Hack the enemy” will become the battle cry for everyone.
Even if (and when) the “official” organizational leaders that champion various causes don’t support the illegal exploits of a few black hat hacker followers, that won’t stop “cause sympathizers” from acting on their behalf against mutual enemies in the same way that Super PACs now help political candidates.
The new mantra: Forget trust — we need to verify the facts. Uncover hypocrisy. Prove your point. Get even. Find the dirt on “those scum.”
There is an evolving definition of right and wrong regarding hacking.
You probably realize that I am not just referring to “noble” or “societal” causes. The natural extension of this is that everyone can potential be hacking everyone else all the time — because we all have causes in which we believe. Causes come in all shapes and sizes; some will likely be for individuals with personal motives.
Not happy with the score of the game? Feel as if justice was not served? Why not hack to see if the other coach somehow cheated. Or, maybe it’s time to get even by revenge hacking.
Didn’t like your work performance appraisal or the raise given? Maybe it’s time to check your supervisors email for something prejudicial (just don’t get caught).
Don’t have the skills to hack alone? There will be hackers for hire — who can help for fun or cash or beliefs similar to yours.
The “hack back” mantra, which was originally thought to be a tool for big banks or other billion-dollar companies to consider against “the foreign bad guy thieves,” will become mainstream.
Some may rejoice at this coming era of new “radical transparency” and “few secrets.” But I am not so sure that the results will be for the better.
I fear not just a loss of privacy, but a less civilized world. A 21st century digital “eye for an eye and a tooth for a tooth” mentality. Hack back may become the societal norm for many situations. The wealthy will spend lots of money on hacking others — for who knows why.
Moving Forward
A few disclaimers. I am not an advocate for this trend. In fact, some will say that what I am describing is not totally new.
I don’t disagree. Hackers for Charity and hacktivists performing denial of service attacks have been around for years. But this cultural shift is dramatically accelerating right now.
Others may say that this commentary is too negative. There is no indication that kids will start to “hack back” rather than just “talking back” to their parents in the future.
My response: I hope you are correct. I hope I am wrong. I don’t like what I’m seeing. I tend to be an optimist, but I am concerned as I connect these data breach story dots.
In summary, the future of hacking into the Internet of Things won’t just be about dollars or identity theft. A new world of hacking motives is starting to emerge — along with convenient, easy to use tools for computer novices to do many dangerous things online.
In a few years, a common question may become: “So, who did you hack this weekend?” Or simply, “What’s your latest cause?” The rest might just be assumed.
Techcrunch: http://tcrn.ch/1TjCVRy


























