China’s Cyber Attacks on Governments and Corporates in Asia
The Chinese government is accused of being behind a newly discovered set of cyber attacks waged against government agencies, corporate companies and journalists across India and Southeast Asia over the past ten years.
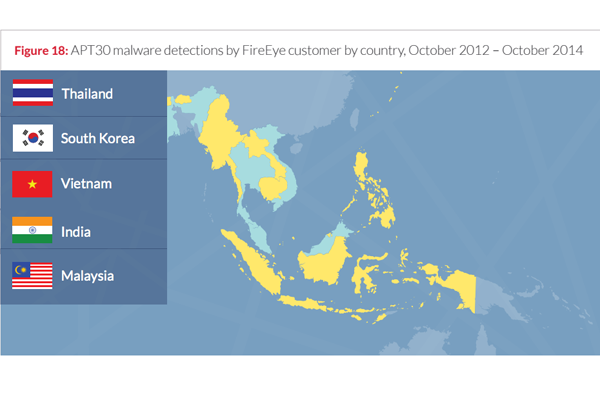
Security firm FireEye released a report today revealing a spate of corporate espionage and cyber spying offenses against targets located in India, Malaysia, Vietnam, Thailand, Nepal, Singapore, Philippines, Indonesia and beyond. The group said attacks began in 2005.
“There’s no smoking gun that shows this is a Chinese government operation, but all signs point to China” FireEye’s APAC CTO Bryce Boland told TechCrunch in an interview. “There’s huge intellectual property development in Asia, that’s the new battleground.”
Boland referenced several pieces of evidence collected by FireEye following “months” of research. In particular, the existence of an operating manual written in Chinese, a code base that was seemingly developed by Chinese developers, and a related domain registered to a suspicious ‘tea company’ in rural China, all imply Chinese involvement.
FireEye’s report caps a rough few days of media coverage for China’s Internet strategy. China put on a (falsely) friendly front when hosted the World Internet Conference last year, but increasingly we hear about its efforts to police the web. Last week, Citizen Lab issued a report detailed Great Canon, a new technology that allows the Chinese government to take down websites — like Github.com — using a worryingly direct and offensive approach.
Of course, it is possible that the attacks highlighted by FireEye were not run directly by the state, and instead by a professional espionage agency, which may have sold secrets to Chinese corporates or even the government itself. Actors are very often a few degrees removed, and concrete evidence is hard to find.
All in all, FireEye detected more than 200 distinction variations of malware developed by the group. The fact that these attacks remained undetected for so long is troubling given the sensitivity of the targets, but there is a positive. Boland explained that because the infrastructure of the attacks had been able to remain similar for years, it isn’t difficult to check on potential compromises and take action if needed.
FireEye shared its report with certain intelligence agencies worldwide in advance of making it public. Though Boland declined to be more specific about exactly which ones had been contacted, he did confirm that FireEye does not provide details of its intelligence or reports to the Chinese government.

























