90% of Android Devices Are DoS Vulnerable
An attacker can trigger the Android vulnerability by sending a malformed video file using the Matroska container.
Less than a week after Trend Micro disclosed a denial-of-service (DoS) vulnerability impacting the majority of Android devices in use, researchers with the security firm have disclosed another DoS flaw that affects even more users.
The vulnerability can be exploited by an attacker to cause a device to reboot, and it is similar to the previously identified bug in that it exists in the media server program, Wish Wu, mobile threat response engineer with Trend Micro, wrote on their blog post.
“In more a severe case, where a related malicious app is set to auto-start, the device can be trapped in an endless reboot and rendered unusable,” Wu wrote, adding that this issue can also cause the device to be drained of its battery life.
An attacker can exploit the bug - CVE-2015-3823, which is caused by an integer overflow in parsing .MKV files - either by a malicious app installed on the affected device, or by luring a user to a specially crafted website containing a malformed media file, Wu wrote.
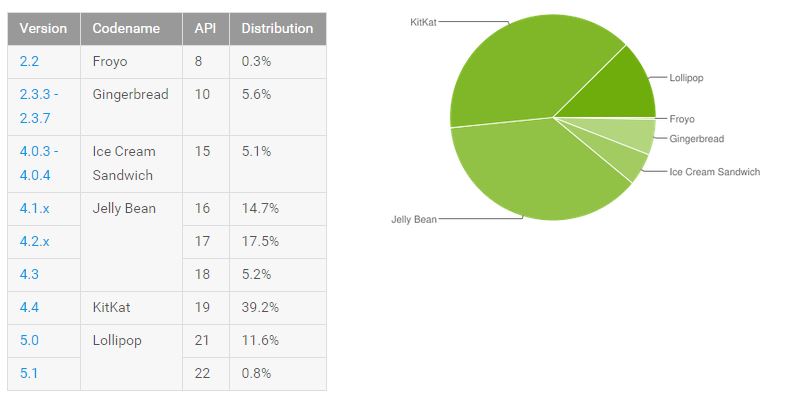
The vulnerability affects Android versions 4.0.1 to 5.1.1, meaning that about 89 percent of devices in use today are affected, Wu wrote, adding attacks exploiting the bug have not been observed in the wild. Trend Micro reported the vulnerability to Google and the Android Security Team confirmed a fix was available.
“Getting rid of the app is quite problematic,” Wu wrote. “It may be difficult to locate the app once downloaded. Attackers may opt to keep it hidden and silent for a long time and only trigger the attack days or months later. Users may believe it is not installed and attribute the reboots to problems in the Android system.”
Denial-of-service bugs are not the only issues plaguing the popular mobile operating system - last week researchers with Zimperium disclosed multiple critical remote code execution vulnerabilities in Android's Stagefright code that can be exploited on an estimated 950 million devices.
SC Magazine: http://bit.ly/1KYVXLi

























